Page 1 of 2
Ghidra - open source reverse engineering tool
Posted: 2021 Feb 26, 20:01
by wwhite
Ghidra is a free and open source reverse engineering tool developed by the National Security Agency.
I've been playing around with Ghidra, similar disassembly to IDA.
I've created the 8061 processor from the 8096 processor. Works well, took a few days to get 100% disassemble my bin.
This would not have been possible without the help of this forum (decipha) and the excellent work of SAD.
The disassembly is a bit of a manual process, and allows you to define different areas of RAM(SFR, General, etc.) and ROM.
The usefulness of this tool is that it shows you C code style disassembly, graphical flow of code, and references to and from routines, and much much more. Actual debugging (like IDA) is not yet possible, but maybe soon. There are many other features, like adding parameters to functions, and setting return values. With memory mapped out, you can set/clear registers, so you can see how the values are used in different parts of the code.
Below is a screen shot, showing the code browser, graph window, register window:
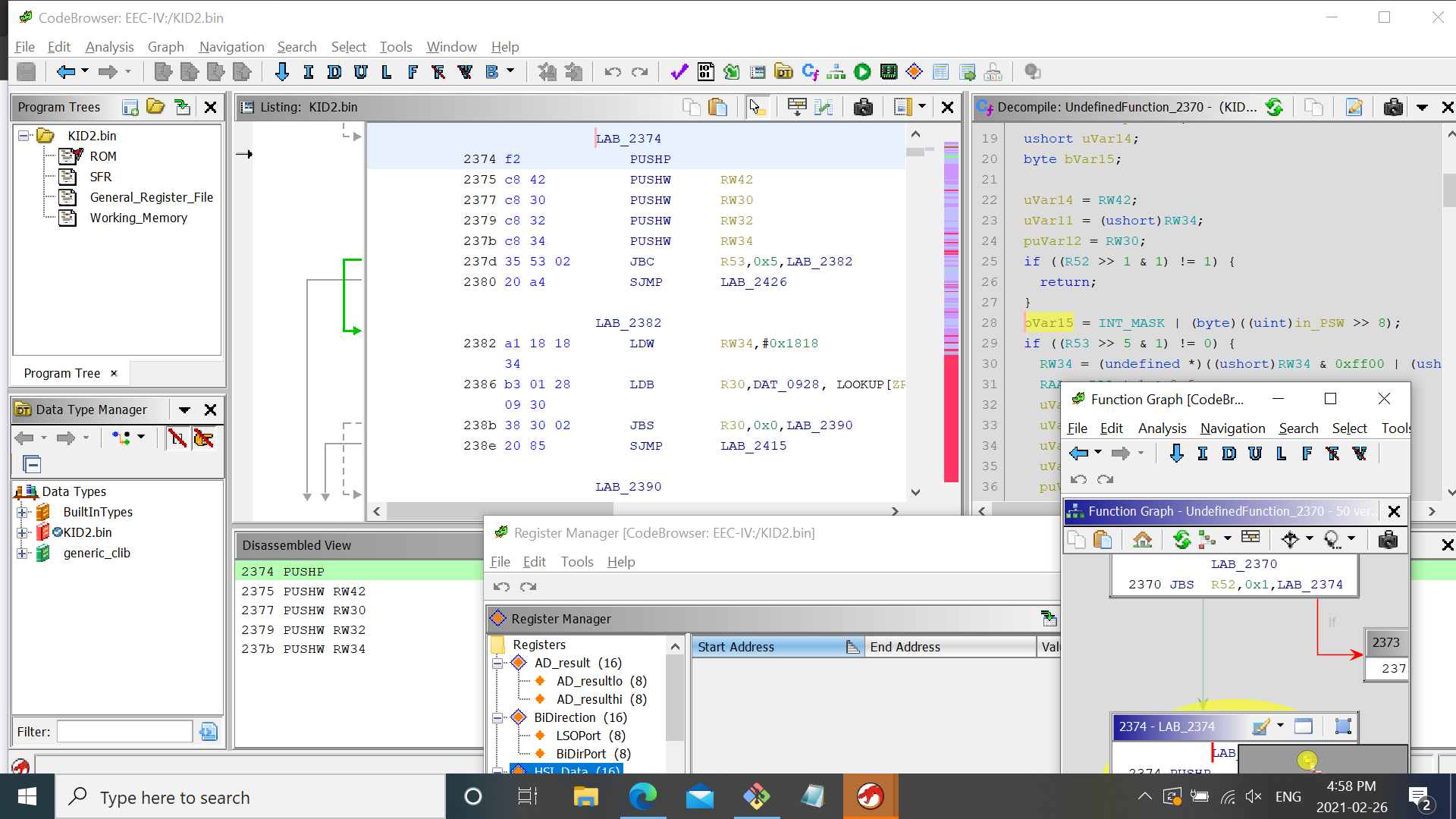
Download image here:
Re: Ghidra - open source reverse engineering tool
Posted: 2021 Feb 26, 22:02
by jsa
Interesting, does it have some sort of config file per processor type that can be shared?
Re: Ghidra - open source reverse engineering tool
Posted: 2021 Feb 27, 02:16
by wwhite
It's a little more complicated than a config file, but yes.
Ghidra uses 'Sleigh', a language for rapid processor specification, as well as 'P-Code', a register transfer language designed for reverse engineering applications.
There are five(5) mandatory files,
- language definitions (.ldefs)
- processor specification (.pspec)
- compiler specification (.cspec)
- sleigh specification (.slaspec)
And those are compiled to create to a .sla file.
I'm writing a readme.md and also working on having the contextual opcode help pop up.
It will be super simple to create another for the 8065 processor as well.
I'll create a new project in github, and post a link here in the next day or two.
Ahh, why wait, here are the files to download:
- 806x.zip
- Ghidra EEC-IV 8061 processor
- (61.12 KiB) Downloaded 365 times
Re: Ghidra - open source reverse engineering tool
Posted: 2021 Feb 27, 07:53
by jsa
Thank you.
Re: Ghidra - open source reverse engineering tool
Posted: 2021 Feb 27, 21:32
by motorhead1991
wwhite wrote: ↑2021 Feb 27, 02:16
It's a little more complicated than a config file, but yes.
Ghidra uses 'Sleigh', a language for rapid processor specification, as well as 'P-Code', a register transfer language designed for reverse engineering applications.
There are five(5) mandatory files,
- language definitions (.ldefs)
- processor specification (.pspec)
- compiler specification (.cspec)
- sleigh specification (.slaspec)
And those are compiled to create to a .sla file.
I'm writing a readme.md and also working on having the contextual opcode help pop up.
It will be super simple to create another for the 8065 processor as well.
I'll create a new project in github, and post a link here in the next day or two.
Ahh, why wait, here are the files to download: 806x.zip
Let me know and I can add you to OpenEEC, as well as fork it over to there
Re: Ghidra - open source reverse engineering tool
Posted: 2021 Mar 02, 19:21
by wwhite
Here is the new repository:
https://github.com/mercury64/Ghidra-EEC-806x
And here are some images to get started after the processor is installed in Ghidra:
1. Create a new project, name it EEC or similar
2. Import your binary
3. Select the language
4. Enter options, hex start address 0x2000, give it a name, ROM
If you make changes to the processor files, you must re-compile them, using:
Code: Select all
./support/sleigh -u -n -a Ghidra/Processors/806x/
Also, you must restart Ghidra to pick up the changes.
Re: Ghidra - open source reverse engineering tool
Posted: 2021 Mar 03, 01:25
by motorhead1991
Added your tool to OpenEEC.

Re: Ghidra - open source reverse engineering tool
Posted: 2022 Aug 14, 20:25
by Jamie from oz
Hi.
Has there been a 8065 processor file done for Ghidra?
Re: Ghidra - open source reverse engineering tool
Posted: 2022 Aug 15, 23:34
by wwhite
Jamie from oz wrote: ↑2022 Aug 14, 20:25
Has there been a 8065 processor file done for Ghidra?
Nope, not yet.
Re: Ghidra - open source reverse engineering tool
Posted: 2022 Aug 16, 05:43
by Jamie from oz
ok.
thanks
